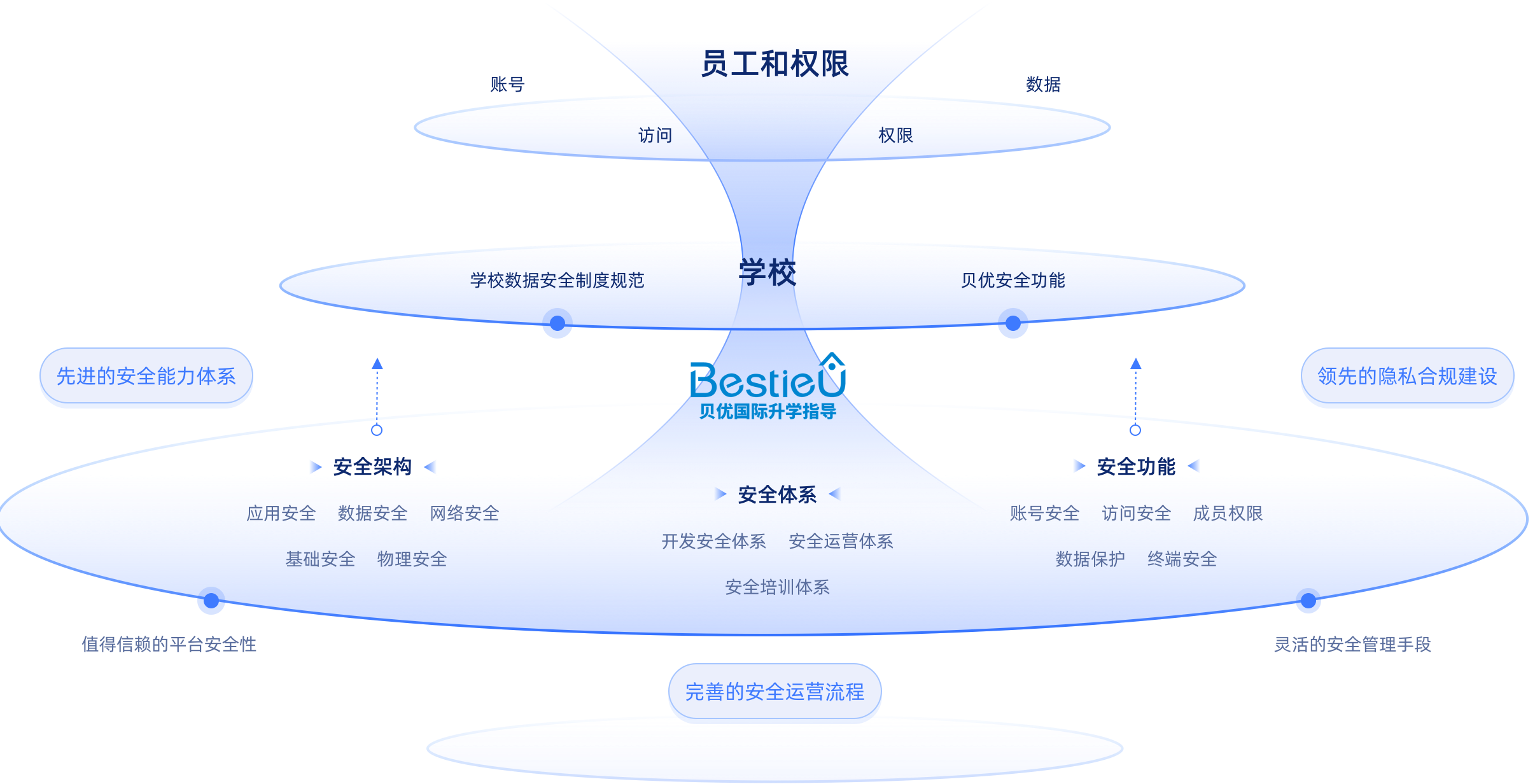
Cooperation begins with trust, and security is paramount above all else.

Your data will not be lost
Our supporting data centers are located in Shanghai and Hangzhou respectively. The business databases are regularly snapshot and backed up, with data storage using a dual-site triple-backup approach, implementing a dual-data double-insurance mechanism: primary storage is on Alibaba Cloud, with backups on Huawei Cloud. Additionally, we have a backup execution monitoring mechanism to ensure the integrity of data backups, and regular backup data recovery tests are conducted.

Your data is exclusively accessible to you
BestieU will allocate unique security keys to each customer, who can also choose a self-managed key scheme. These keys are used to encrypt customer data, ensuring that data is encrypted before storage. Not only is customer data isolated from each other, but BestieU internally cannot access customer data. If you require our assistance in configuring your system, authorization from you is needed to add authorized accounts to your system.

Your data security is guaranteed
BestieU has implemented stringent security protection and management solutions at every stage of data collection, transmission, and storage, covering various encryption measures and full-process monitoring. Any anomalies are detected and addressed promptly to ensure data security throughout its lifecycle. Core sensitive data is encrypted using the AES advanced encryption algorithm, and confidentiality agreements are signed with each client.
 Su Public Network Security No. 32010602010884
Su Public Network Security No. 32010602010884
















@2x.png)
@2x.png)
备份@2x.png)
@2x.png)
@2x.png)

